Microsoft continues to enhance XDR capabilities every day. To use this comprehensive security solution more effectively, the M365DefenderStuff module has been developed, providing IT professionals and security managers with essential capabilities. In this article, we’ll delve into the capabilities, commands, and outputs of the M365DefenderStuff module.
Capabilities of the M365DefenderStuff Module
1. Threat Detection and Response
M365DefenderStuff enhances the threat detection and response capabilities provided by Microsoft 365 Defender. The module allows you to obtain detailed information about devices and software, helping to identify potential security vulnerabilities. For example, you can examine the security status of devices and detect weaknesses.
2. Advanced Reporting
The module offers comprehensive reporting features. You can generate detailed reports on security incidents, threats, and response actions. These reports can be customized for presentation to managers and stakeholders. Additionally, the module supports the automatic generation and email delivery of reports at specified intervals.
3. Automated Security Operations
M365DefenderStuff helps automate your security operations. For instance, when a specific threat is detected, you can ensure that certain actions are taken automatically. This might include locking user accounts, blocking specific IP addresses, or quarantining certain files.
4. Advanced Analysis
The module enables advanced threat analysis by analyzing data from Microsoft 365 Defender. It helps identify threat vectors, attack patterns, and potential vulnerabilities. These analyses allow you to enhance your security strategies to prevent future attacks.
Install M365DefenderStuff module
To be able to use my PowerShell commands, you must first install the M365DefenderStuff module from the PowerShell Gallery.
Install-Module M365DefenderStuffTIP: to get all available commands run the following command in your PowerShell console:
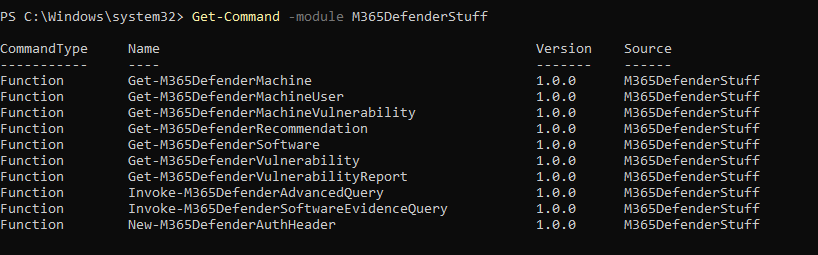
Get-Command -module M365DefenderStuff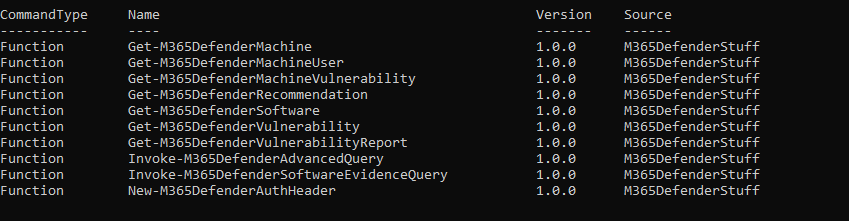
Authenticate
Import-Module Az.Accounts
Connect-AzAccountCommands of the M365DefenderStuff Module
The M365DefenderStuff module offers a wide range of commands. Here are the most commonly used commands and their descriptions:
Get-M365DefenderMachine
This command lists all devices registered with Microsoft 365 Defender and provides detailed information about them. You can view the security status and other important details of the devices.
Get-M365DefenderMachine
Get-M365DefenderMachine -MachineID 'c5fb6ee86d04e75e9ba1c96412d55e9108639952'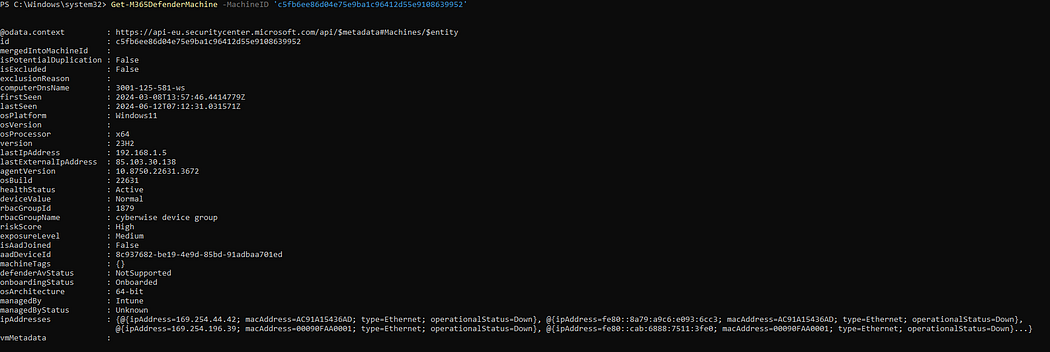
Get-M365DefenderMachineUser
This command provides information about the users who have logged into a specific device. It is useful for tracking which users are logging into which devices.
Get-M365DefenderMachineUser -MachineId 'c5fb6ee86d04e75e9ba1c96412d55e9108639952'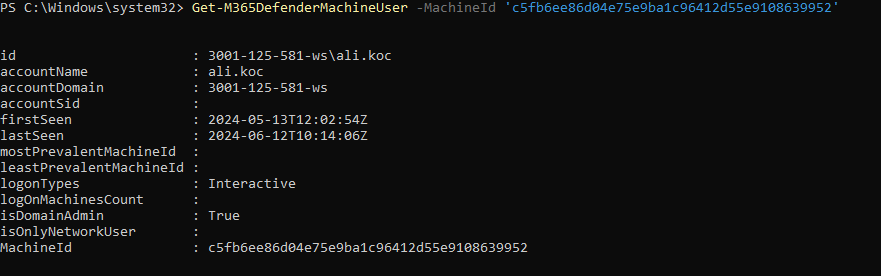
Get-M365DefenderMachineVulnerability
This command lists the security vulnerabilities on a specific device. You can determine the weaknesses of the device and take necessary measures.
# get all found vulnerabilities (can take several minutes to complete!)
Get-M365DefenderVulnerability
# get details of specific vulnerability
Get-M365DefenderVulnerability -vulnerabilityId 'c5fb6ee86d04e75e9ba1c96412d55e9108639952'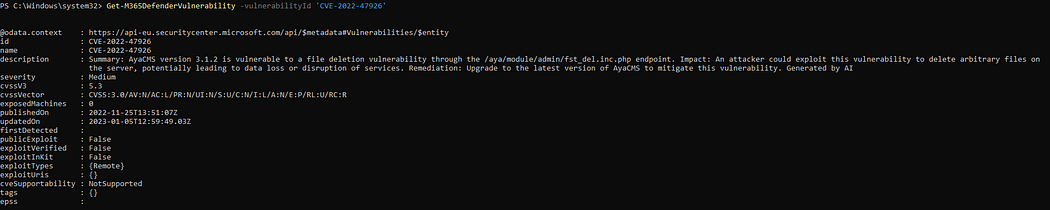
Generate vulnerability report
This command generates a detailed report on security vulnerabilities. The report includes details of the weaknesses and recommended actions to mitigate them.
# get just software vulnerabilities of CTRITICAL type and group them by machine
Get-M365DefenderVulnerabilityReport -groupBy machine -skipOSVuln -severity Critical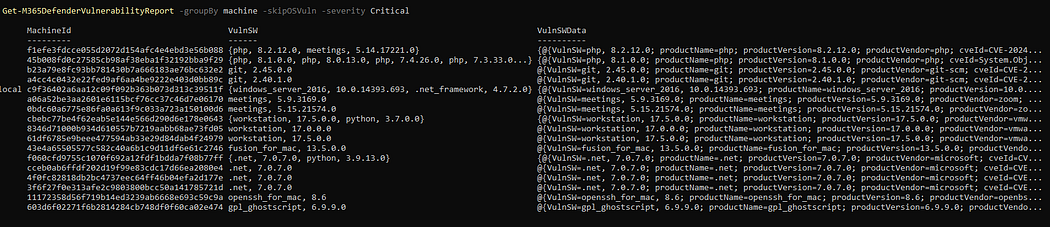
Get-M365DefenderRecommendation
This command provides recommendations to improve security status and mitigate threats. You can view the security advice provided by Microsoft 365 Defender.
# get all security recommendations
Get-M365DefenderRecommendation
# get security recommendations just for Putty software.
Get-M365DefenderRecommendation -productName 'putty'
# get all security recommendations for given machine.
Get-M365DefenderRecommendation -machineId 'c5fb6ee86d04e75e9ba1c96412d55e9108639952'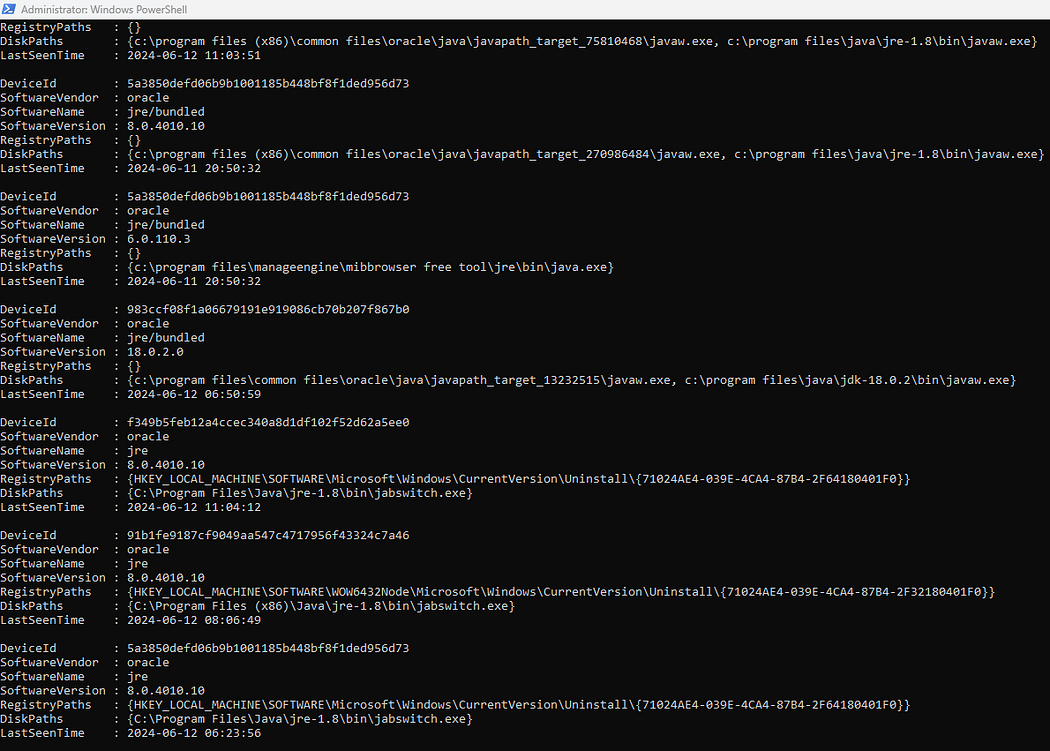
Get-M365DefenderSoftware
This command provides information about the software installed on devices. You can examine which software is installed and its security status.
# get all detected applications
Get-M365DefenderSoftware
# get just specific application
Get-M365DefenderSoftware -softwareId 'adobe-_-creative_cloud'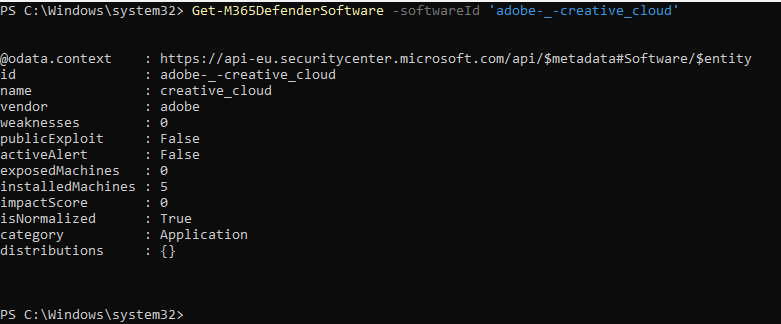
Invoke-M365DefenderAdvancedQuery
This command allows you to perform advanced queries in the Microsoft 365 Defender database. You can conduct detailed searches and analyses based on specific criteria.
Invoke-M365DefenderAdvancedQuery -Query "DeviceEvents | where Timestamp > ago(7d)"Invoke-M365DefenderSoftwareEvidenceQuery
This command allows you to query evidence and details related to specific software. You can evaluate the security status and potential threats of the software.
Invoke-M365DefenderSoftwareEvidenceQuery -appName JRE
New-M365DefenderAuthHeader
This command creates the necessary authentication headers for communicating with Microsoft 365 Defender APIs. It ensures authentication in your API calls.
New-M365DefenderAuthHeader -ClientId "YourClientId" -ClientSecret "YourClientSecret" -TenantId "YourTenantId"Outputs of the M365DefenderStuff Module
The M365DefenderStuff module generates various outputs that help improve your security operations:
- Threat Reports: Detailed reports on security incidents, providing information on the type, source, affected systems, and actions taken.
- Security Dashboard: Real-time security dashboards displaying all security threats and incidents on a single screen.
- Automated Alerts: The module sends immediate alerts when specific threats or anomalies are detected. These alerts can be delivered via email, SMS, or other communication channels.
- Analysis Reports: Advanced analysis reports providing in-depth information on attack vectors, vulnerabilities, and preventive measures.
- Incident Response Reports: Detailed reports on all actions taken during the incident response process and the outcomes of those actions.
Conclusion
The M365DefenderStuff module extends the capabilities of Microsoft 365 Defender, helping organizations protect more effectively against cyber threats. With advanced reporting, automated security operations, and detailed analyses, IT and security teams can adopt a more proactive approach. By using this module, you can enhance your organization’s security posture and respond more quickly and effectively to potential threats.
thanks to Doitpshway